Support - Latest News and Updates
Information on this page is updated often.
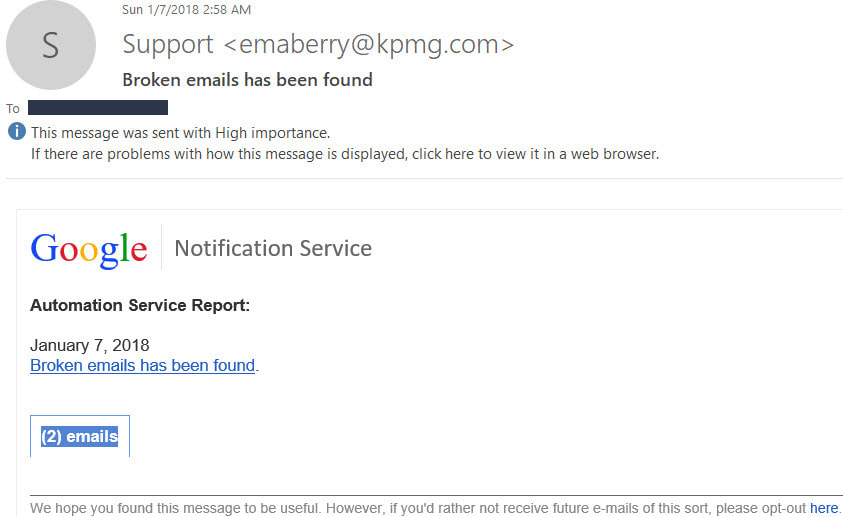
1/7/18 Fake Emails: "Your computer has been infected, please call Microsoft Immediately"
|
Be aware of fake emails that look legit. Look at who sent it, if it looks suspicious, delete it immediately (Shift Delete can permanently delete it). This email looks like it is from Google, but if you look at the email address at the top it is from <[email protected]>.
There are several going around right now that if you click on the link or just open it, it will give you a message that your computer has been infected, please call Microsoft and they give you a number. DO NOT CALL THE NUMBER! They will tell you there is something wrong and they need access to your computer and/or a credit card to fit it.
If you have any questions or need more information let me know. JoLynn |
1/5/18 Spectre and MeltdownMicrosoft - Details you need on those big chip flaws:
Design flaws in processors from leading chipmakers could let attackers access sensitive information. How could that happen, and what's the fix? The vulnerabilities, revealed Wednesday (1/3/18), could let an attacker capture information they shouldn't be able to access, like those passwords and keys. That's why an attack on a computer chip can turn into a serious security concern. Protect your device against chip-related security flaws Microsoft is aware of the recently discovered security flaw that impacts chips from several different manufacturers. Many devices and applications will be affected by this flaw, including any operating systems such as Windows that run on the affected chips. To get all available protections, get the latest updates for both software and hardware. Take the following steps:
Information from CNET: What can I do to protect myself? As chipmakers and computer companies roll out software updates, be sure to install them. Beyond that, since hackers would have to install malware on your computer, do your best to make that harder for them. That means you should keep all your other software updated, including your web browsers and Flash (if you're still using it). Also, run security software to make sure you don't have any malicious software on your computer right now. Finally, look out for phishing emails. Emails that trick you into clicking on a link and downloading malicious software are still the number one way for hackers to get a foothold on your computer. |
Websites for more details:
https://meltdownattack.com/
https://www.cnet.com/news/spectre-meltdown-intel-arm-amd-processor-cpu-chip-flaw-vulnerability-faq/ When you buy a computer, phone, etc. make sure you take the time to register the item. This will ensure that you will receive the latest information on flaws, updates, new releases, etc. |